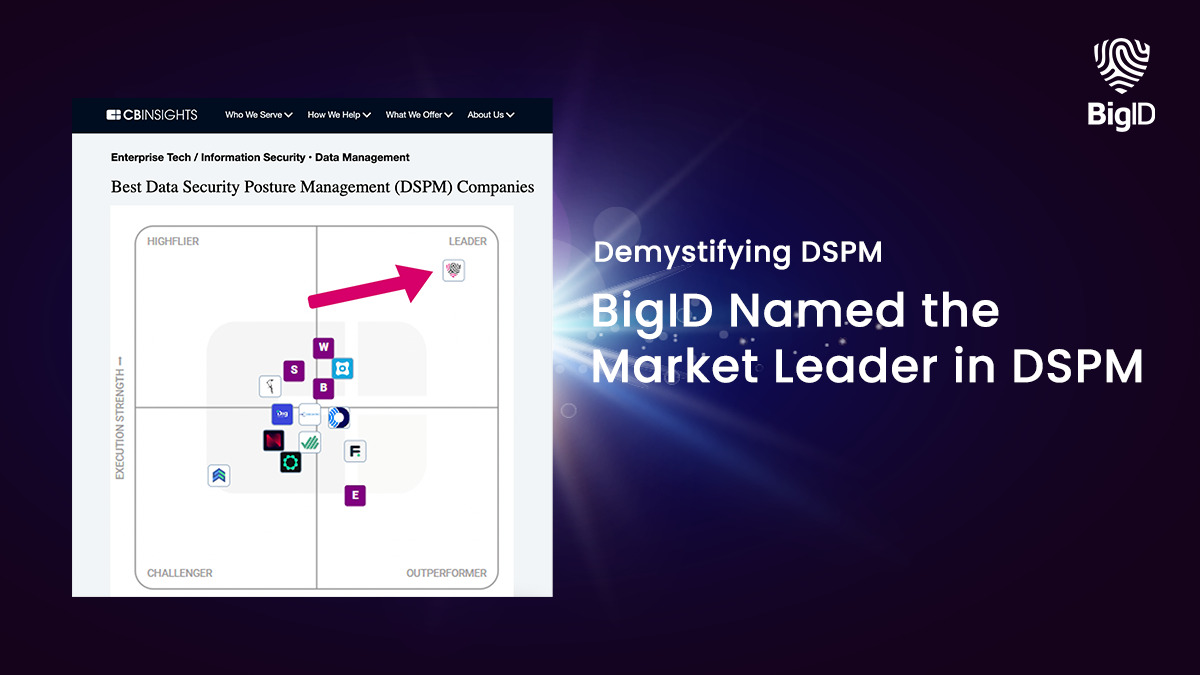
Unlocking DSPM security is a crucial aspect of modern technology, designed to protect sensitive data and mitigate potential risks. DSPM, also known as Data Security and Privacy Management, focuses on safeguarding information through various security measures. With the ever-growing cyber threats and data breaches, ensuring robust DSPM security has become a necessity for businesses and individuals alike.
One unique fact about DSPM security is its comprehensive approach towards protecting data. It encompasses various measures, including encryption, access control, data masking, and monitoring, to ensure optimal security. These measures help prevent unauthorized access, protect data integrity, and maintain confidentiality. Moreover, DSPM security not only safeguards data stored within an organization but also during its transmission across networks and systems.
Explore more: Insights on DSPM Security
Moving forward, let’s explore some key takeaways regarding DSPM security. Firstly, we will delve into the importance of robust encryption protocols to protect sensitive data from unauthorized access. Secondly, we will discuss the significance of access control mechanisms that regulate and monitor the access to data within an organization. Lastly, we will examine the benefits of data masking techniques, which anonymize sensitive information, reducing the risk of data breaches. By understanding these key takeaways, businesses can unlock the potential of DSPM security and ensure the safety of their valuable data.
key Takeaways
1. DSPM security requires a holistic approach: Protecting Digital Supply Chain Process Management (DSPM) security involves the implementation of a comprehensive security strategy that covers all stages of the supply chain, including identification, authentication, authorization, encryption, and monitoring.
2. Threats to DSPM security are diverse and evolving: The increasing digitization of supply chain processes has exposed new vulnerabilities to cyber threats, including unauthorized access, data breaches, malware attacks, and supply chain manipulation. Organizations must remain vigilant in adapting their security measures to counter these evolving threats.
3. Secure development practices are crucial: Implementing secure development practices is essential to minimizing vulnerabilities in DSPM processes. This includes conducting regular security assessments, patching system vulnerabilities, utilizing secure coding techniques, and adopting a secure development lifecycle (SDL) approach.
4. Collaboration and information sharing enhance DSPM security: Sharing information and collaborating with industry peers, third-party vendors, and government bodies can provide valuable insights and strengthen DSPM security practices. Establishing trusted relationships, participating in security communities, and staying up-to-date with the latest threat intelligence are vital for proactive security management.
5. Continuous monitoring and response are imperative: Employing a robust monitoring system that enables real-time threat detection and incident response is critical for effective DSPM security. Regularly reviewing audit logs, network traffic analysis, and endpoint security data can help identify anomalies, prevent security breaches, and mitigate their impact in a timely manner.
How to Unlock DSPM Security: A Deep Dive into Insights?
Understanding DSPM Security
DSPM stands for Digital Signal Processing and Modulation, and it plays a crucial role in ensuring the security of digital communications. In this section, we will explore the fundamentals of DSPM security and how it works.
The Importance of DSPM Security
With the increasing reliance on digital communication platforms, the security of DSPM systems is of utmost importance. In this section, we will discuss why DSPM security is essential and the potential risks associated with inadequate security measures.
Common Security Vulnerabilities in DSPM Systems
Despite the advancements in DSPM security, there are still several vulnerabilities that malicious actors can exploit. This section will delve into the most common security vulnerabilities found in DSPM systems and provide insights on how to mitigate these risks.
Best Practices for DSPM Security
Implementing robust security measures is crucial for ensuring the integrity and confidentiality of DSPM systems. This section will explore the best practices that organizations can follow to enhance the security of their DSPM systems.
Emerging Trends in DSPM Security
As technology continues to evolve, new trends and developments emerge in DSPM security. In this section, we will discuss some of the latest advancements in DSPM security and how they can be leveraged to enhance overall system security.
Conclusion
By diving deep into insights on DSPM security, we have gained a comprehensive understanding of the importance of securing digital communication systems. Implementing robust security measures and staying updated with emerging trends are key to safeguarding DSPM systems from potential threats.
5 Tips to Enhance DSPM Security:
- Regularly update and patch DSPM software to ensure it is protected against the latest security vulnerabilities.
- Implement strong access controls and authentication mechanisms to prevent unauthorized access to DSPM systems.
- Encrypt sensitive data transmitted through DSPM systems to maintain confidentiality.
- Train employees on DSPM security best practices and establish policies to promote a security-conscious culture within the organization.
- Conduct regular security audits and penetration tests to identify and remediate potential vulnerabilities in DSPM systems.
Frequently Asked Questions
1. What is DSPM security?
DSPM security stands for Data Science Platform for Manufacturing security. It is a comprehensive system designed to protect manufacturing processes and data from unauthorized access and cyber threats.
2. Why is DSPM security important for businesses?
DSPM security is crucial for businesses as it ensures the integrity, confidentiality, and availability of sensitive manufacturing data. It helps prevent data breaches, intellectual property theft, and production disruptions, ultimately safeguarding brand reputation and customer trust.
3. How does DSPM security work?
DSPM security combines various technologies and processes, including access controls, encryption, network segmentation, intrusion detection systems, and security audits, to create a robust defense against potential threats. It continuously monitors and analyzes data to identify anomalies and potential risks.
4. Can DSPM security be integrated with existing manufacturing systems?
Yes, DSPM security solutions are designed to be compatible with existing manufacturing systems and can be integrated seamlessly. This allows businesses to enhance their security posture without disrupting production processes.
5. Are DSPM security solutions scalable?
Absolutely, DSPM security solutions are highly scalable and can be tailored to meet the specific needs and size of any manufacturing environment. Whether you are a small manufacturer or a large enterprise, there are solutions available to fit your requirements.
6. How does DSPM security help with compliance?
DSPM security solutions typically include features that help businesses comply with industry regulations such as GDPR, ISO 27001, and NIST. These solutions ensure proper data governance practices, document access controls, and provide robust audit trails for compliance reporting.
7. Can DSPM security protect against insider threats?
Yes, DSPM security systems are designed to detect and mitigate both external and internal threats. They employ advanced analytics and machine learning algorithms to identify anomalous behaviors and flag potential insider threats, allowing businesses to take appropriate action.
8. How does DSPM security handle cloud-based manufacturing systems?
DSPM security solutions can be seamlessly integrated with cloud-based manufacturing systems. They monitor data flows to and from the cloud, implement encryption and access controls, and provide real-time threat detection and response capabilities.
9. What is the cost of implementing DSPM security?
The cost of implementing DSPM security varies depending on several factors, including the size of the manufacturing environment, the complexity of existing systems, and the level of security required. It is best to consult with security professionals to determine the most cost-effective solution for your business.
10. Can DSPM security solutions be customized?
Yes, DSPM security solutions can be customized to cater to the specific needs of each manufacturing organization. Security providers often offer flexible options and modules that can be tailored to address unique challenges and requirements.
Final Thoughts
Unlocking DSPM security is becoming increasingly essential in today’s fast-paced and interconnected manufacturing landscape. With the rise of cyber threats and the need to protect sensitive data, businesses must invest in robust security measures. DSPM security provides comprehensive solutions to safeguard valuable manufacturing processes and data from both external and internal threats. By implementing DSPM security, businesses can ensure data integrity, protect intellectual property, and maintain a competitive edge.
However, it is important to recognize that DSPM security is not a one-time investment. As technology evolves and threats continue to emerge, it is crucial to regularly update and enhance security measures. Ongoing monitoring, employee training, and collaboration with security experts are vital for maintaining a strong security posture. By staying proactive and adaptive, businesses can unlock the full potential of DSPM security and mitigate the risks associated with digital manufacturing.